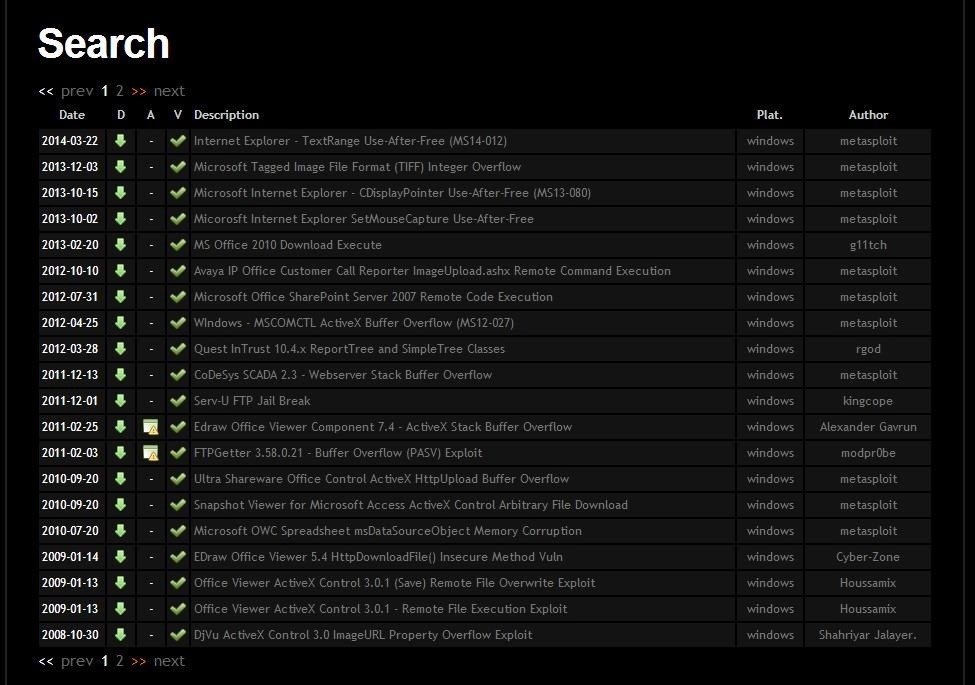
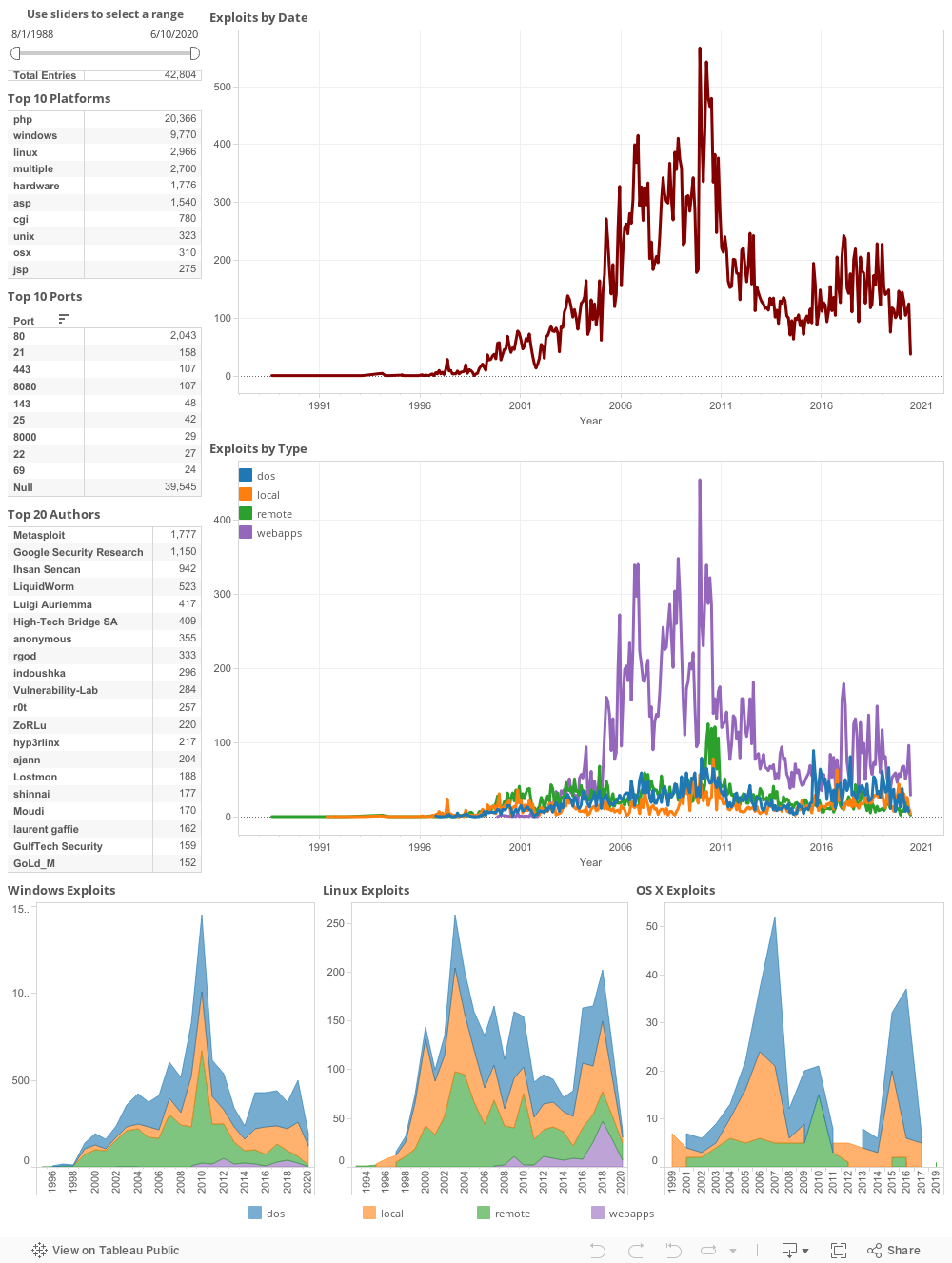
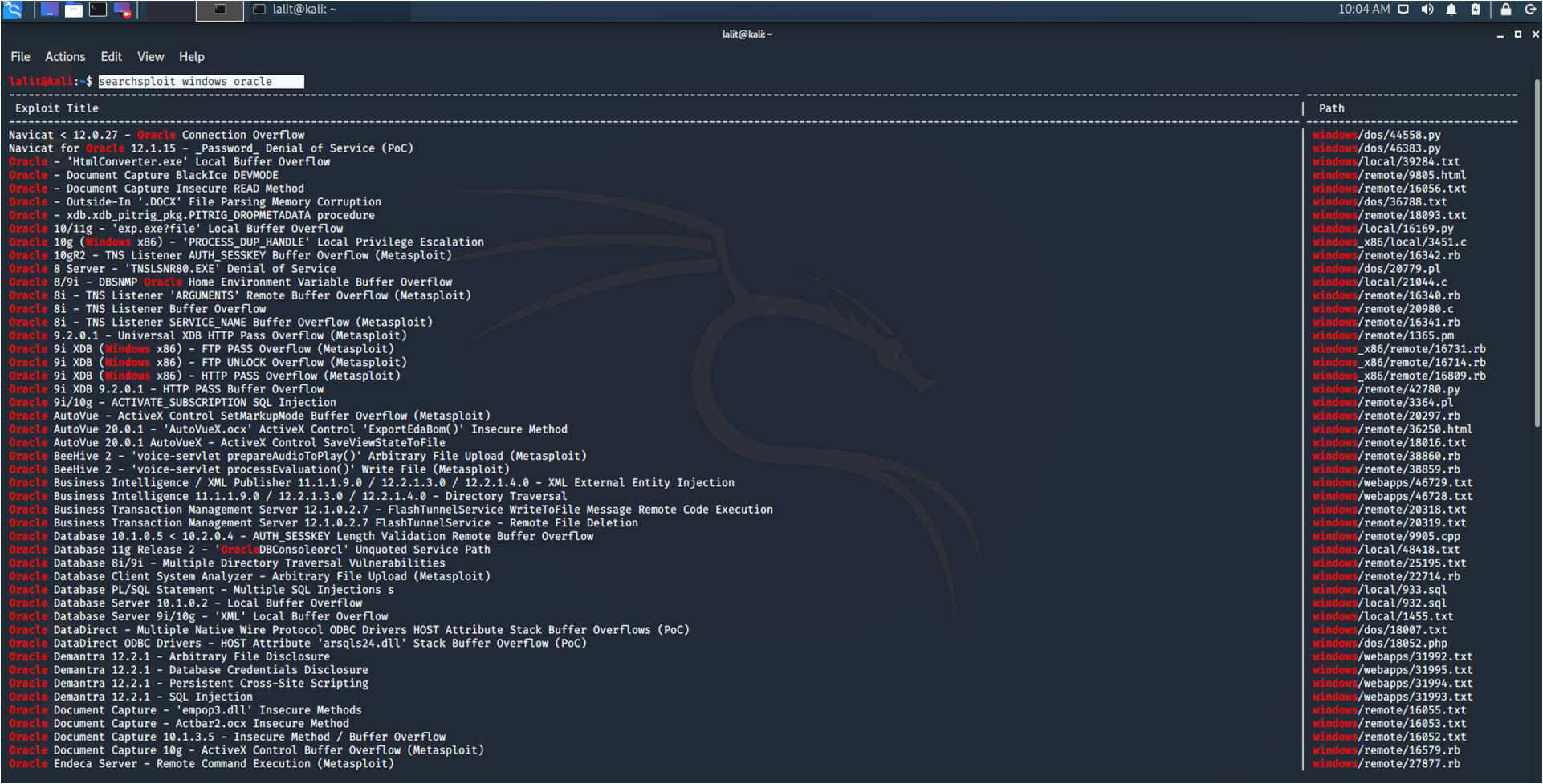
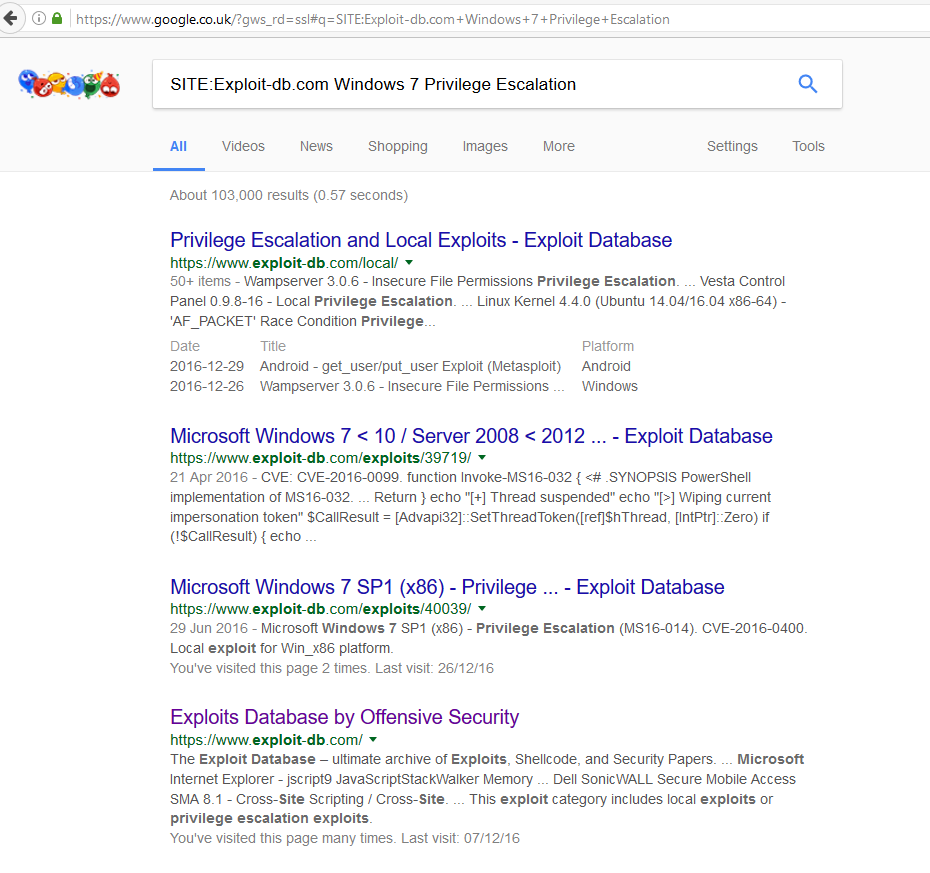
GitHub - offensive-security/exploitdb-papers: The legacy Exploit Database paper repository - New repo located at https://gitlab.com/exploit-database/ exploitdb-papers

Web Security Geeks - The Security Blog: Exploiting Software Based Vulnerabilities : Attacking Network - Pentesting Network
![PDF] Generating Informative CVE Description From ExploitDB Posts by Extractive Summarization | Semantic Scholar PDF] Generating Informative CVE Description From ExploitDB Posts by Extractive Summarization | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a8137e4986bc0590e583752edfd4df64f159577e/1-Figure1-1.png)